Advanced settings (Linux)
Archiving
Archiving is not activated as standard.
The following setting options are available when activated:
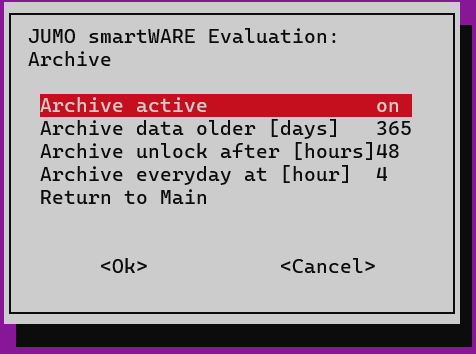
The settings have the following meaning:
Setting | Value | Meaning |
|---|---|---|
Archive active | On | Archiving is active. |
Archive data older [days] | 365 | All device data older than 365 days is archived. |
Archive unlock after [hours] | 48 | If a user has restored data from the archive, this data is automatically deleted from JUMO smartWARE Evaluation after 48 hours. The data is retained at all times in the archive. |
Archive everyday at [hour] | 04 | Archiving is carried out daily at 4 am. |
The data for archiving is saved in the "~/smartWAREArchive" directory. A relevant link must be created in Linux for this directory to link to another hard disk drive.
The changes are confirmed with "OK".
Data backup
Data backup is not activated as standard.
The following setting options are available when activated:
The device process data is also saved in the "~smartWAREBackup/datastore" directory when backup is activated at the point when the data is recorded in Datastore.
The time for performing data backup is 4 am. The configuration data for JUMO smartWARE Evaluation is then saved daily at 4 am in the "~smartWAREBackup/dataview" and "~smartWAREBackup/datareport" directories.
The data backup data is then saved in the "~/smartWAREBackup" directory. A relevant link must be created in Windows® for this directory to link to another hard disk drive.
The changes are confirmed with "OK".
Activating the changed parameters
The generated .env file is saved under "~/smartWARE_452.5.0.0.14/.env".
The settings are first accepted in the system when JUMO smartWARE Evaluation is next started.
”~/smartWARE_452.5.0.0.14/stop_smartware.sh”
”~/smartWARE_452.5.0.0.14/start_smartware.sh”
The HTTPS protocol in the JUMO Jupiter device is only supported from firmware version 8.x and above. Installing the JUMO smartWARE Evaluation software on a cloud computer on the Internet should therefore only be considered with HTTPS support from firmware version 8.x and above.
Certificates
A certificate is required to run JUMO smartWARE Evaluation in the browser. A self-signed certificate is generated and copied to the "~/smartWAREData/reverse_proxy/certs" directory during installation.
If the user interface of the software GUI in the browser is opened using the HTTPS protocol, Windows® displays a warning message. This warning appears as the self-signed certificate of the browser is not classified as trustworthy.
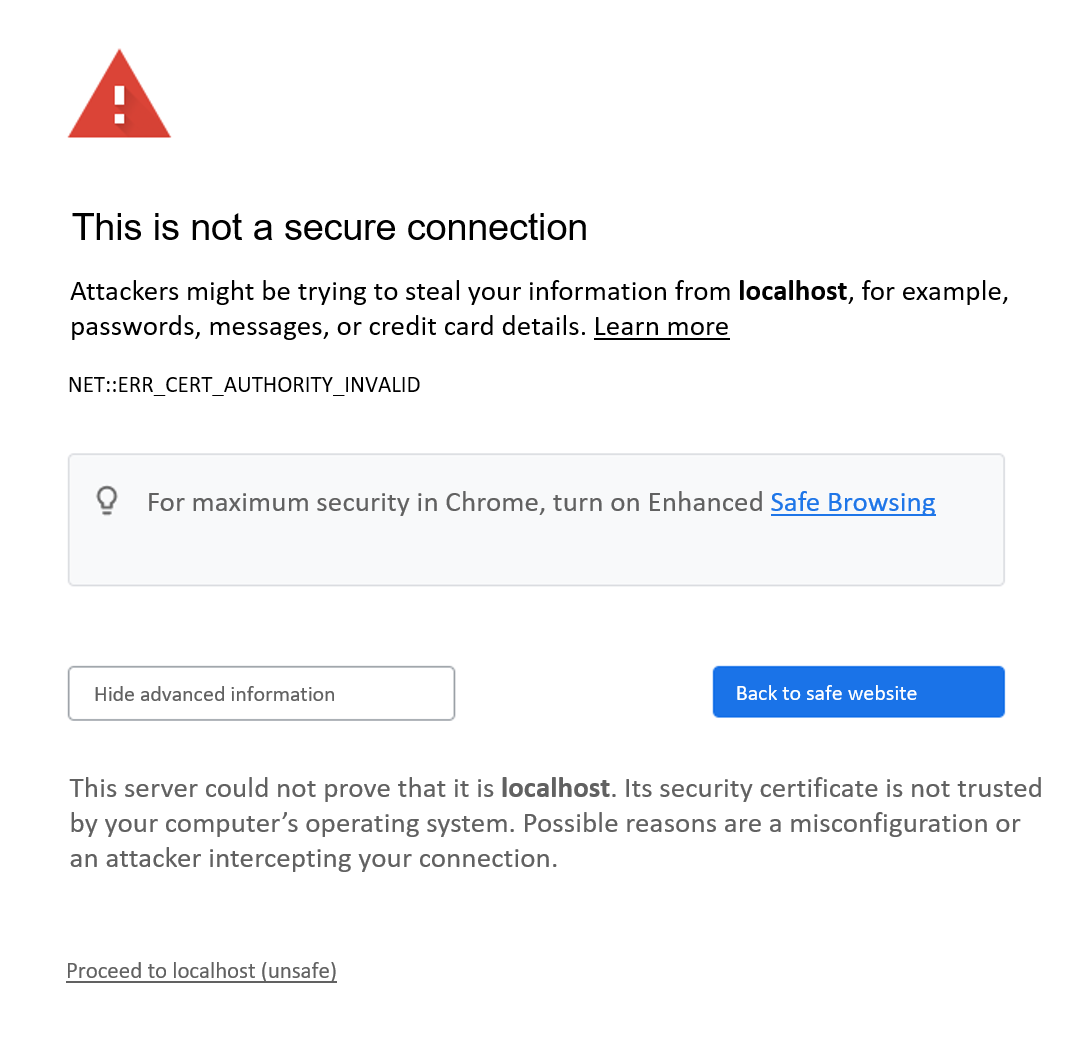
This message can be ignored by clicking on "Proceed to localhost (unsafe)".
So that the warning is not shown again when the page is called up, a signed certificate can alternatively be used.
There are two files in the "~/smartWAREData/reverse_proxy/certs" directory:
smartware.crt
smartware.key
These files can only be replaced if the user has root rights (sudo).
These certificate and key files can be replaced with the company's own, officially signed files. To do so, the JUMO smartWARE software must be stopped.
The two existing files must be renamed (e.g. as "smartware.crt_original" and "smartware.key_original"). The officially signed files must then be copied to the "~/smartWAREData/reverse_proxy/certs" directory and, if necessary, renamed.
The files must have the designations "smartware.crt" and "smartware.key" and be available in the PEM or X509 format.
After the files are replaced and the JUMO smartWARE services are started, the log file should be checked to ensure that the replaced files do not cause any problems:
cat ~/smartWAREData/reverse_proxy/error.log | more