A Keycloak system is located behind the normal Authorization Concept of JUMO smartWARE SCADA, which takes over cross-user management as IAM.
At the start, only the "root" user is available
Access to the Keycloak administration console
-
Enter SCADA-URL into the web browser with the ending /auth: https://Hostname/auth/
-
Click on "Administration Console"
-
Log in with user = "root" and password = root password

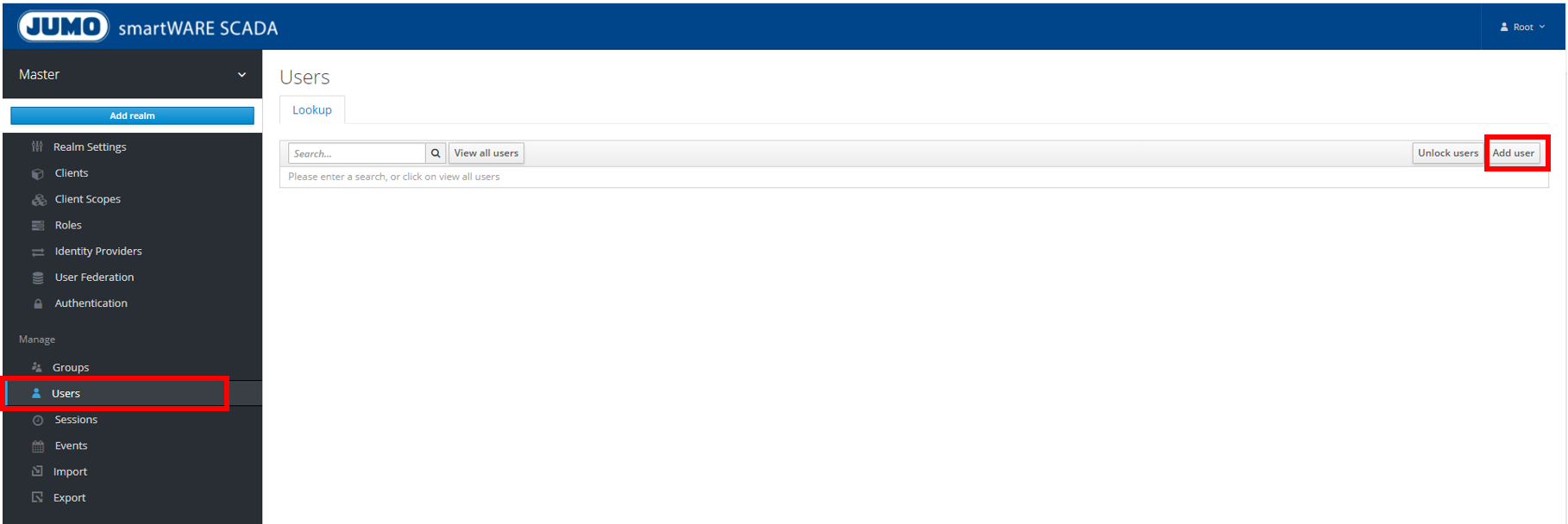
Creating additional users and view all users
-
Manage → Users → Add user
-
The following entries are necessary and subsequently confirmed with "save":
-
User name
-
First Name (optional: but useful to find the user in central administration again)
-
User Enabled → ON
-
Email Verified → ON
-
-
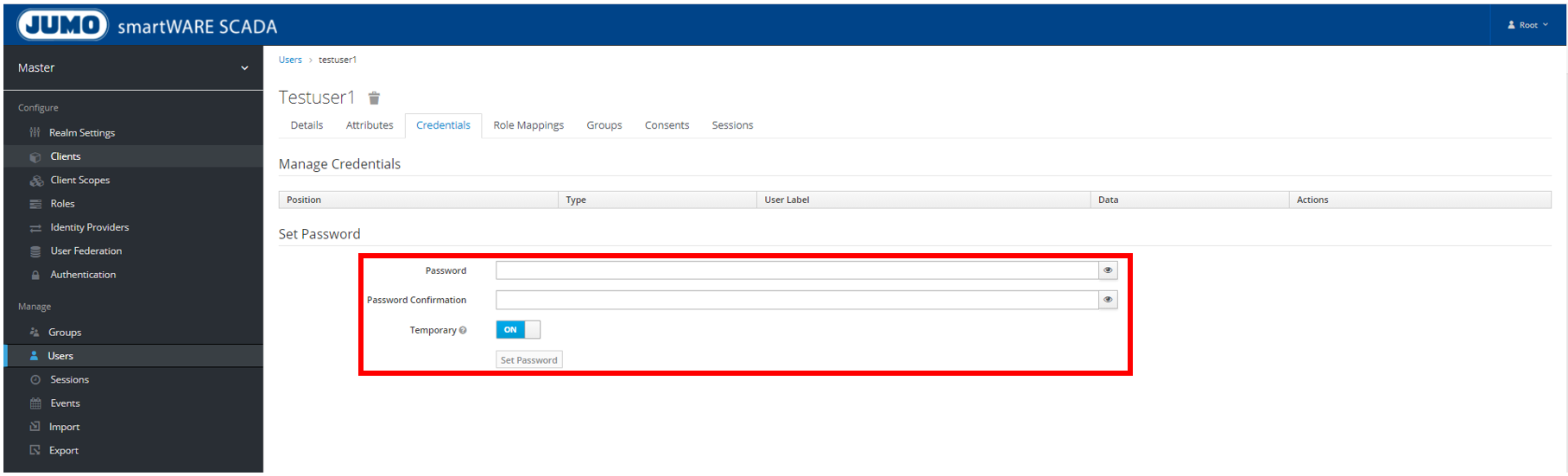
Allocate password
-
Allocate password under "Credentials" and confirm with "Set Password"
-
Under "Temporary" → OFF (i.e. the user is not asked again to change password)
-
-
Checking whether or not the user was created:
-
Users → View all users
-
It is always helpful to hover over the question marks within Keycloak to get additional information.
"Single Sign On" concept: One user name and one password for all applications
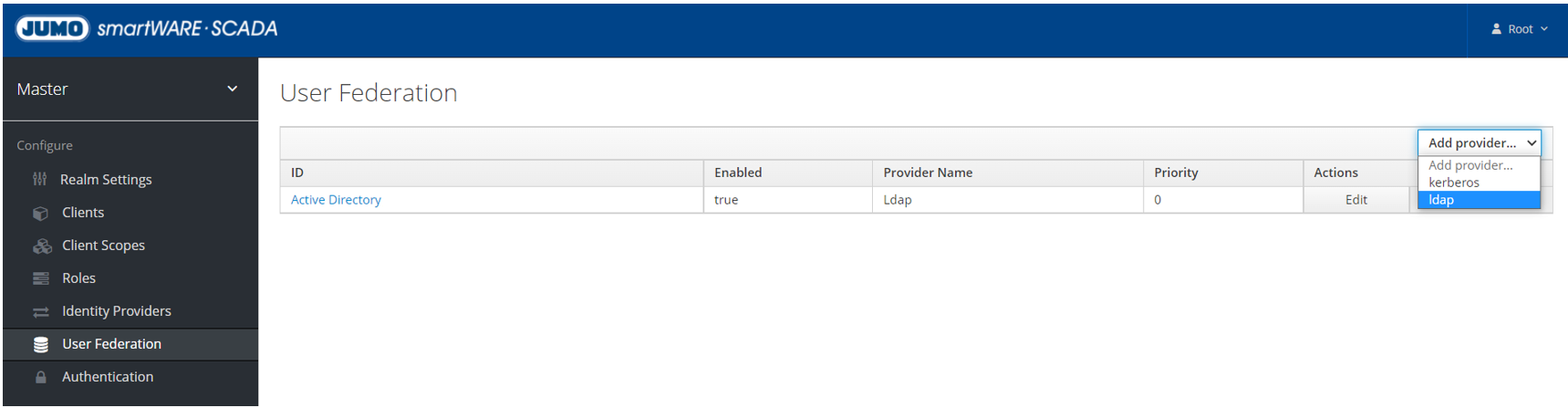
Linking SCADA user management with a company-own user management
-
Go to "Add provider" in the Keycloak console and make a selection under "User Federation":
-
Option 1: LDAP connection
-
Option 2: Kerberos
-
-
Subsequently, provide all necessary and desired settings
-
Afterwards, every user within the set provider can access the SCADA application with a known user name and password.
Changing log-in settings
-
User Registration → Here you can set that users must register in order to access the SCADA application.
-
Edit user name → Off
-
Forgot password → If this function is active and an email server is set up in Keycloak, the forgotten password function can be used.
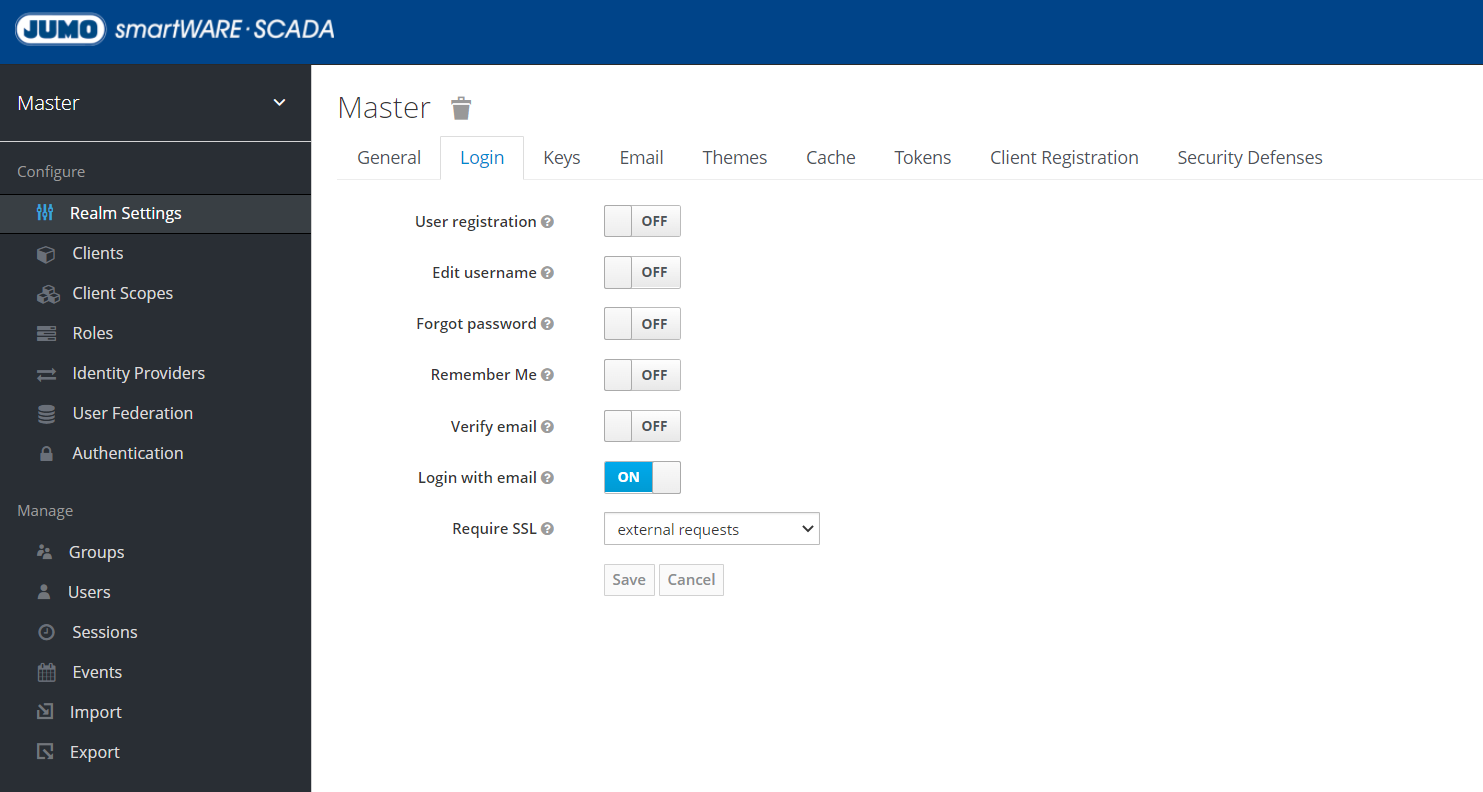
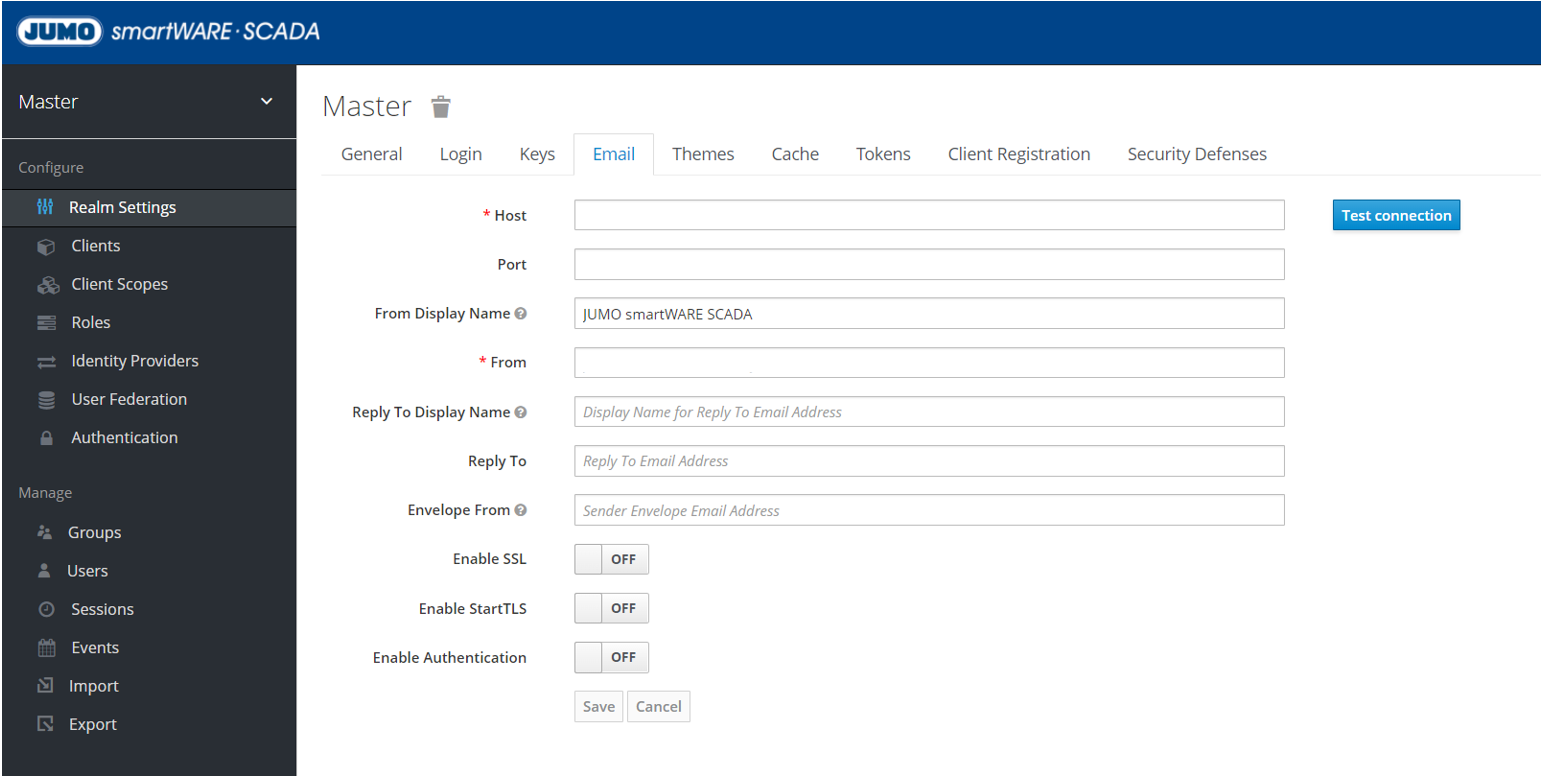
Set up email server for verification
This is required, for example, if the forgotten password or email verification function is to be used. Generally, if the Keycloak console is to send mails.
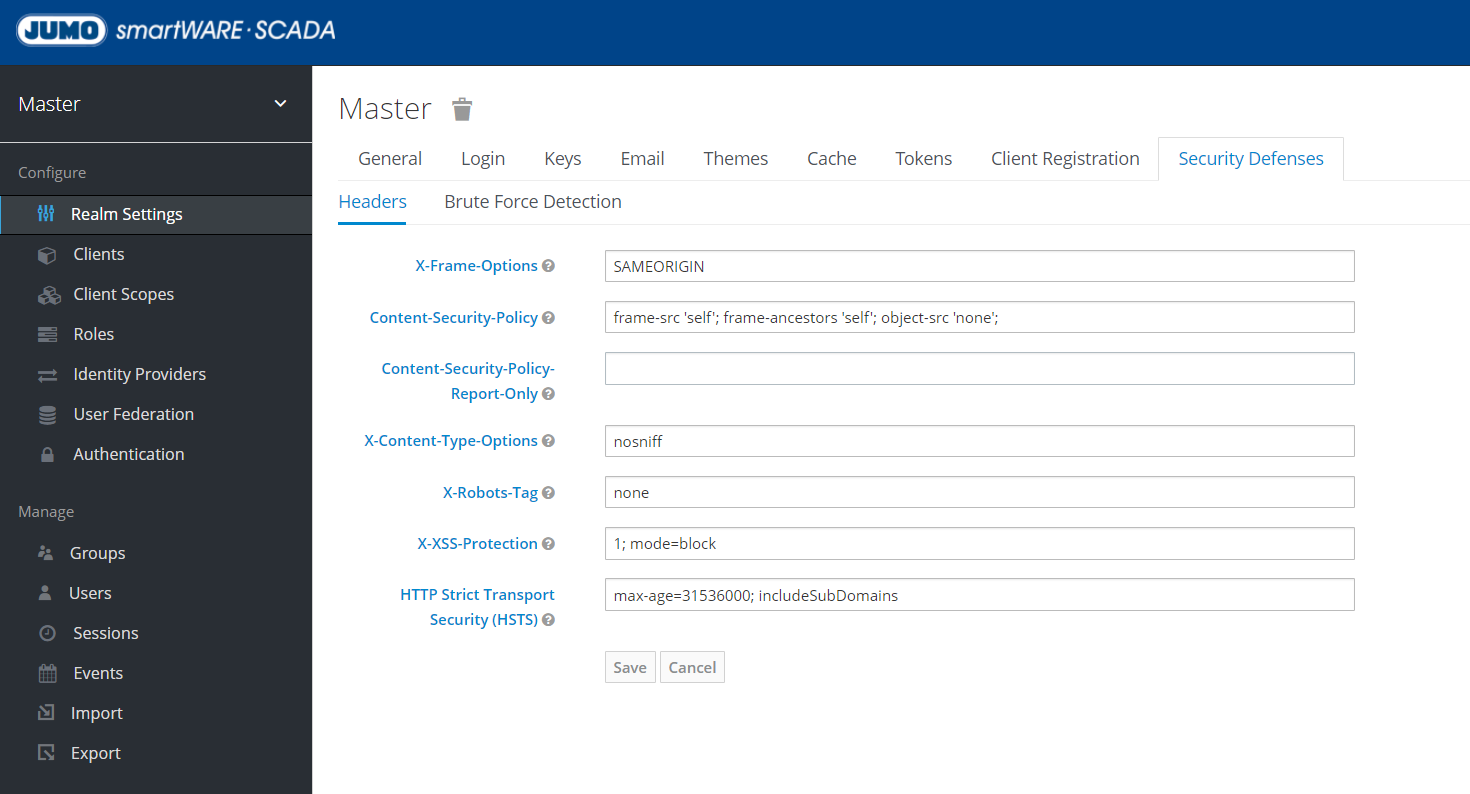
Setting safety and password guidelines
Security and password policies can be set under these sections:
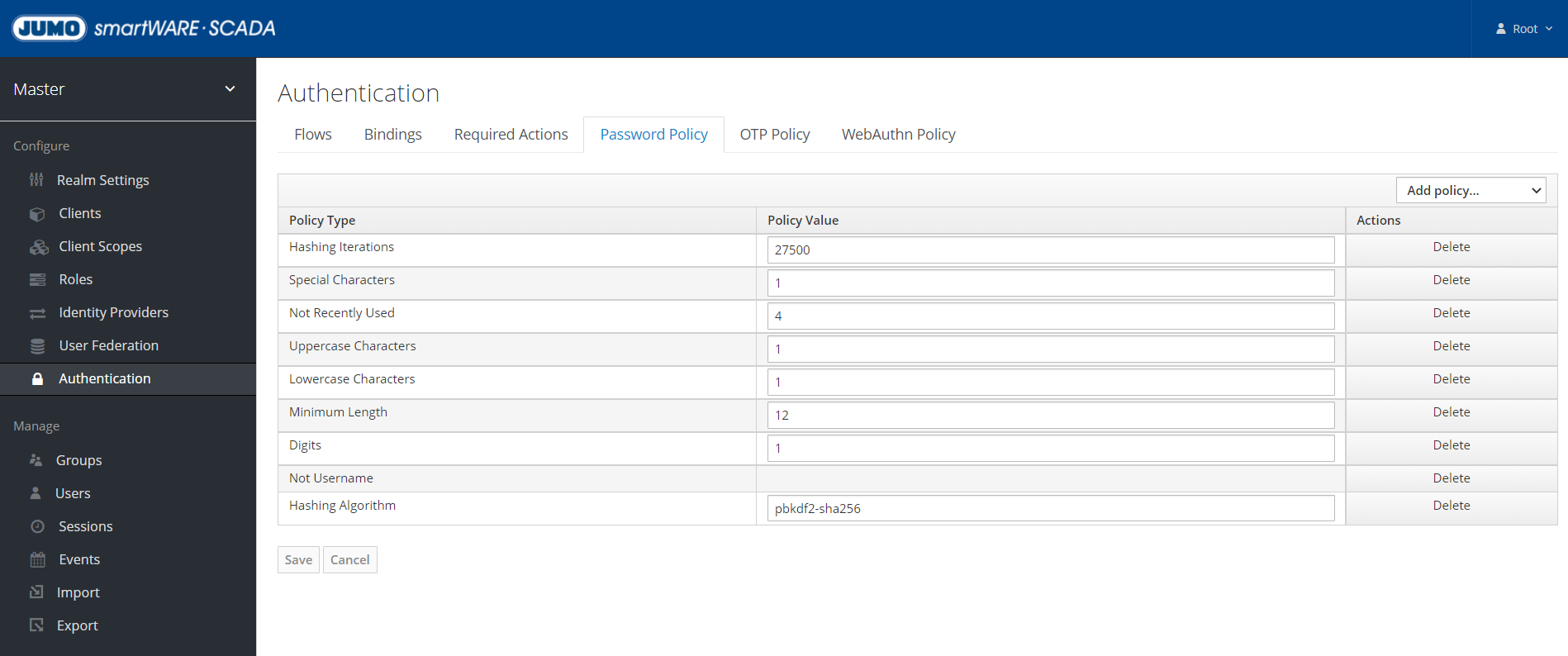
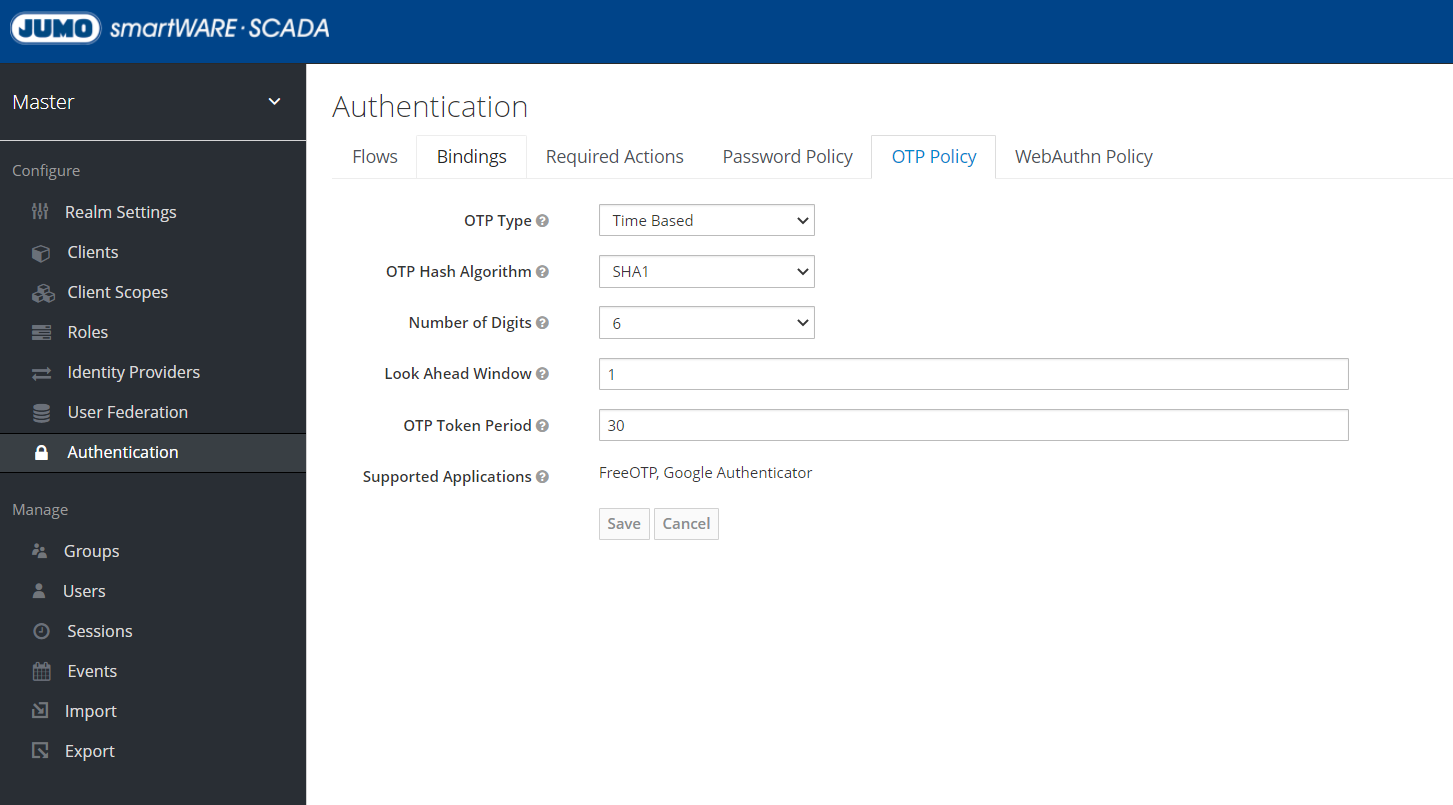
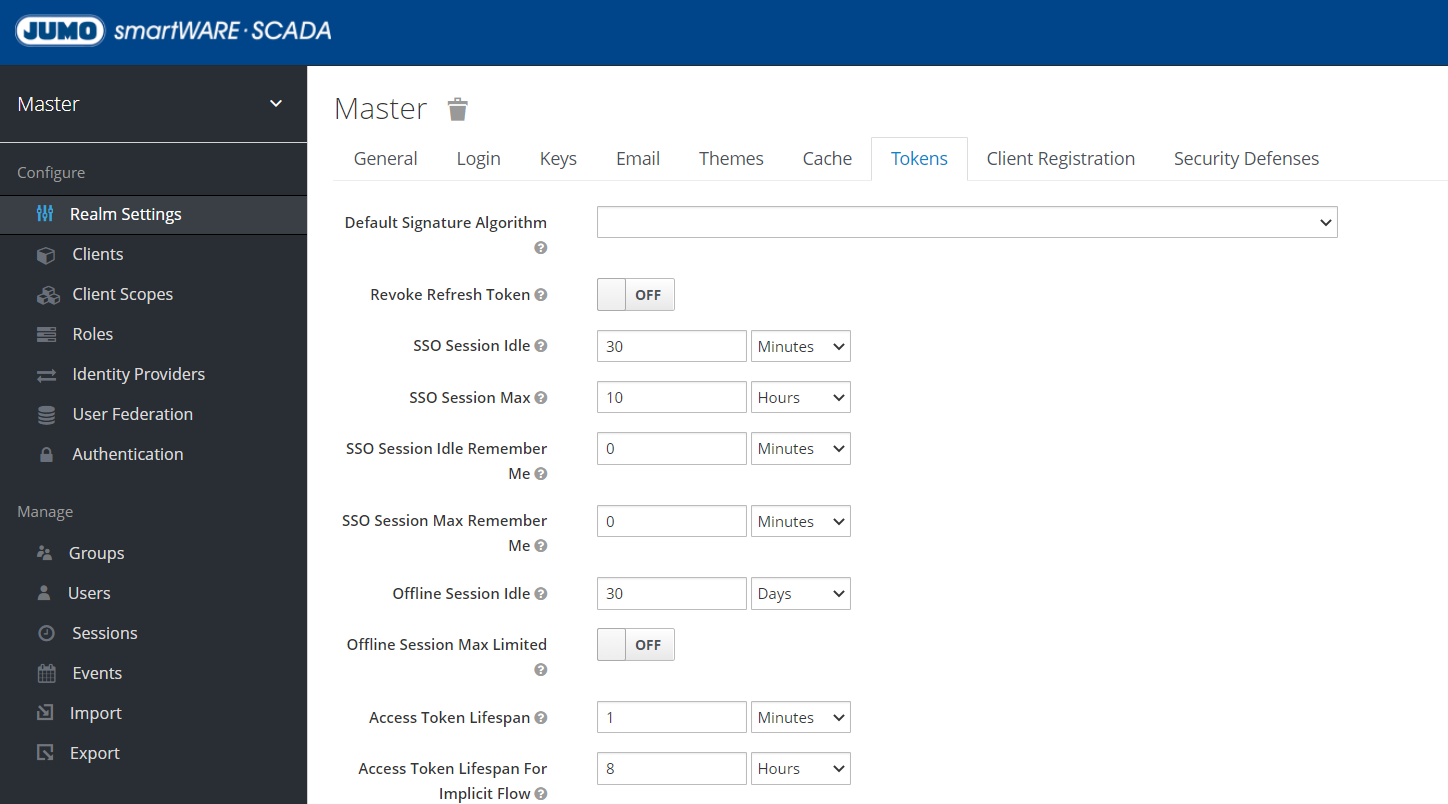
Changing token settings
Here you can set, among other things, how long the session remains active in the browser before the system automatically logs you out and prompts you to log in again: "Access Token Lifespan For Implicit Flow".